The Strategic Importance of OT Network Cabling
Industrial control systems are at the heart of modern production and infrastructure management. The security of OT networks is critical not only for data integrity and network performance but also for operational continuity and safety. Cabling design is a key strategic element that should not be overlooked when planning OT networks.
When properly implemented, this design prevents the spread of cyber threats, isolates critical systems, and ensures uninterrupted operations. For example, in a power plant, if turbine control systems and the management network are connected via the same physical segment, a single cyber attack could halt the entire operation. However, if these systems are divided into separate segments and supported by redundant cabling paths, the attack affects only one segment while other operations continue uninterrupted. This approach directly supports one of the primary security objectives of OT networks: limiting attacks and preventing lateral movement.
Cabling design is not limited to segmentation alone. Physical security ensures that cables and devices pass through controlled access areas. This prevents unauthorized personnel from directly accessing equipment, reducing the likelihood of cyber attackers manipulating the system through physical access. Physical access violations in OT networks are a significant starting point for cyber threats. Especially in production and energy facilities, unauthorized access to cables or key devices increases the risk of malware injection or system manipulation. Therefore, cabling design must be planned in conjunction with physical security measures; locked cabinets, secure rooms, and controlled access areas form the foundation of this integration.
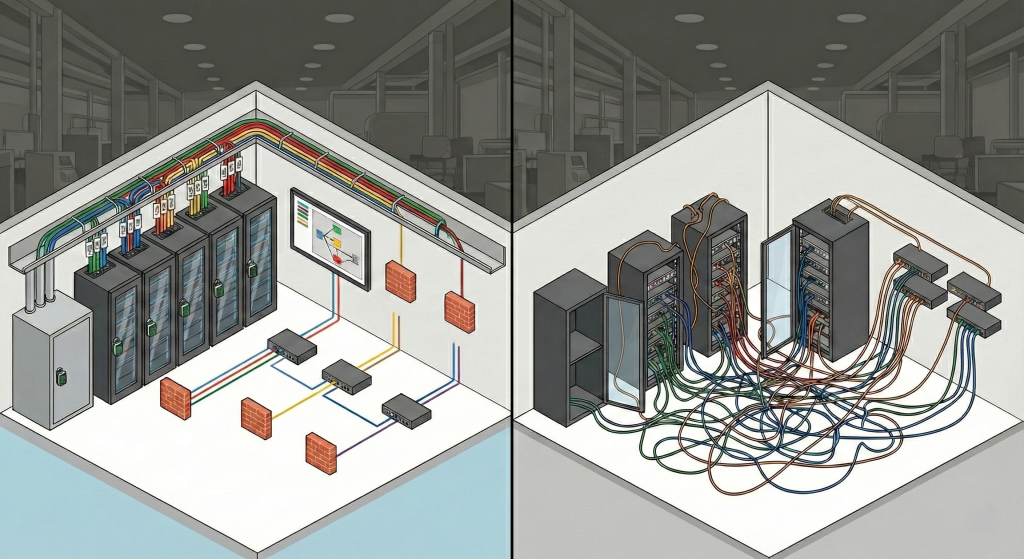
Network Segmentation and Isolation
One of the most critical elements of OT network cabling design is network segmentation. When critical production equipment, management networks, IoT devices, and guest devices are placed in separate cabling segments, breaches in one segment cannot spread to others. Segmentation not only limits cyber attacks but also allows for better network traffic management and rapid anomaly detection. For example, in a manufacturing facility, if PLCs and SCADA systems are cabled in separate segments, compromising a single device affects only that segment. The management network, data analysis systems, and IoT devices remain unaffected. This design dramatically enhances OT network security and preserves operational continuity.
Alongside segmentation, redundancy is a critical factor. Designing alternative cabling paths for critical devices and data routes ensures that the system remains resilient to both cyber attacks and technical failures. If a cable or connection fails, data transmission continues via alternative paths, and operational processes remain uninterrupted. This feature is especially vital in industries such as manufacturing, energy, and transportation, where downtime is extremely costly. Redundant cabling design not only improves security but also guarantees operational reliability and business continuity.
Integration of Physical and Digital Security
OT cabling design integrates physical security measures with digital protection mechanisms. Routing cables through secure areas, placing critical devices in locked cabinets, and integrating access control systems prevent attackers from physically manipulating the network. At the same time, segmentation and redundancy limit the spread of digital threats. This holistic approach ensures that security in OT networks is not a one-time measure but a continuously managed process. Proper documentation, labeling, and management of every cable and connection facilitate rapid detection of cyber threats and swift response. Inadequately labeled or undocumented cables may create hidden pathways for attackers, making planned and manageable cabling essential in OT networks.
In modern OT networks, the strategic role of cabling design extends beyond limiting attacks; it also optimizes network management and prepares systems for future threats. Compliance with cabling standards such as IEC 61850, TIA-568, and ISO/IEC 11801 guarantees data transmission performance while supporting infrastructure critical to security. Well-documented and labeled cables enable easier analysis of potential cyber threats and allow preemptive identification of system vulnerabilities.
Cable Types in OT Networks and Security Strategies
The selection of cable types in cabling design is also crucial for security. High-bandwidth, low-latency cables ensure the performance of critical production and control systems. Additionally, cables resistant to electromagnetic interference and environmental factors provide physical protection to the system. Routing critical cables through separate segments and secure pathways reduces both cyber and operational risks. For instance, fiber optic cables are often preferred for critical PLC and SCADA connections due to their resistance to electromagnetic interference and minimal data loss. Copper cables, on the other hand, are used for short-distance connections and redundant paths, balancing cost and security. Correct cable selection and integration with segmentation increase OT network resilience and minimize the impact of cyber threats.>
A proper and resilient cabling infrastructure in OT networks not only acts as a barrier against cyber attacks but also enhances physical and operational resilience. You can find the details of this strategic approach in our article, The Role of Cabling Infrastructure in Industrial Cyber Resilience.

Frequently Asked Questions
1. What is the impact of cabling design on cybersecurity in OT networks?
Cabling design in OT networks isolates critical systems and implements network segmentation, preventing the spread of cyber attacks. A properly designed cabling infrastructure strengthens both physical and digital security and ensures uninterrupted operational processes.
2. Why is network segmentation important in OT systems?
Network segmentation places critical production equipment, management networks, and IoT devices in separate cabling segments. This ensures that a cyber attack in one segment does not spread to others, keeping critical processes in the system operational.
3. Which standards should be used in OT cabling design?
International standards such as IEC 61850, TIA-568, and ISO/IEC 11801 should be applied in OT cabling design. These standards guarantee cable performance while supporting network manageability and cybersecurity.
4. Why is physical security important in cabling design?
Routing critical cables and devices through locked cabinets or secure rooms prevents unauthorized access to the system. Since a large portion of cyber attacks on OT systems starts with physical access, this measure significantly reduces the risk of intrusion.
5. How is redundancy and fault tolerance achieved in OT networks?
Redundant cabling paths and alternative connection routes ensure that if a cable fails or a segment is compromised, the system automatically switches to backup paths. This allows data transmission and operational processes to continue uninterrupted, minimizing the impact of cyber attacks.